Crypto Networks and Proof of Stake vs Proof of Work – Part 2, Energy & Security
Recently the Loki Project approved their Loki Improvement Proposal (LIP) #5 which suggests moving Loki from a Proof of Work (PoW) based network to a Proof of Stake (PoS) network due to implementation of checkpointing and the diminishing role that miners would have in the network. Feel free to read up on this proposal, as it is packed with lots of good research and substantiating evidence to support such a change. There has also been talk for some time now about the Ethereum network moving from PoW to PoS with a new Ethereum 2.0, or ProgPoW, or something – no one seems to know.
I felt it was an appropriate time to write an article comparing the two systems for the sake of broadening the conversation and contributing the all projects that are struggling with PoW vs PoS. Hopefully every one of us involved in the blockchain ecosystem will continue the dialog and support the greater good and advancement of these wonderful projects.
As the Director of Mining operations for Distributed Ledger, it’s easy for me to quickly step into the PoW category – because that’s what I do, I am a miner! However, it’s a little more complex than that and it helps to be able to remove yourself from a personal passion to focus on what benefits not only the project and the digital blockchain environment, but the entire crypto adoption movement. It is through this lens that I attempt to present the differences and benefits of PoW vs PoS, in a three-part series.
Did you miss Part 1?
But doesn’t PoW mining ruin the environment with its power-hungry demands?
I hear this question a lot, and for a time I thought it was probably true until I investigated the numbers. On the surface, the network hash rates are always climbing so naturally there must be more power being consumed. This would be true with static mining hardware (I am focusing strictly on ASIC hardware here because it provides the bulk of the arguments basis) but we all know bigger and better models are always coming out. In fact, these new models are always striving to achieve more efficiency, so while the hash rates climb the cost in J/TH/s (Joules per Terahash per second) is trending down. The scary truth is that the traditional banking system uses far more.
In fact, the world banking system alone uses roughly 6 times more electricity than all crypto mining combined; gold mining uses more than twice the amount of energy as crypto miners. Even more interesting is due to the nature of energy costs, most of the crypto mining energy consumed comes from renewable resources. I have included a chart build by Tyler Bain, PE, CBP, with United Power. He shared this information recently at a blockchain training conference in Denver, Co.
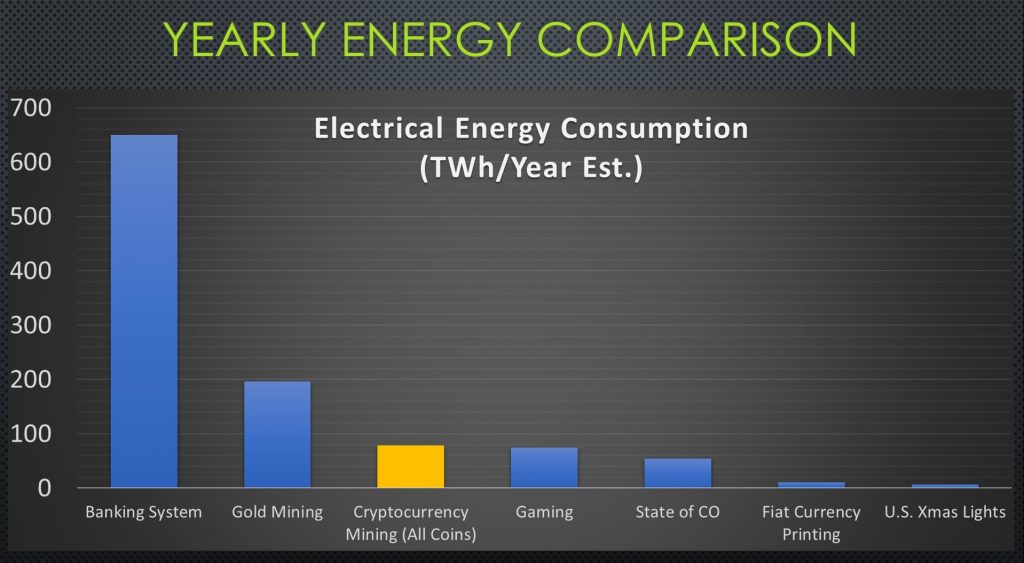
Figure 1: Credit – Tyler Bain, PE, CBP | References: https://www.academia.edu/37178295/The_Cost_and_Sustainability_of_Bitcoin_August_2018_
https://www.iea.org/newsroom/news/2019/july/bitcoin-energy-use-mined-the-gap.html
https://coinshares.co.uk/research/bitcoin-mining-network-june-2019
PoW mining is just a waste of electricity
Another very common statement we all hear often, but I would argue so are your Christmas lights you string up every year (most of us would probably agree, even if we do enjoy it). In fact, considering a lot of wealth has been created from crypto mining, I cannot understand how people would view that as wasteful and in the same category. Whom the wealth flows to is irrelevant to the fact that actual wealth has been generated, and therefore it is not a waste of resources. How do we justify the massive quantities of electricity consumed by the traditional banking system? Is that not considered a waste because we use money every day, or is it because we didn’t realize the staggering numbers until they are graphed out for us? Cryptocurrencies are now used in transactions every day for goods and services as well, just not to the same scale as fiat currencies. I think the better argument would be not how to reduce energy consumption, but how to generate it more efficiently and in greater quantities. We will never stop consuming energy and as societies grow and advance, they will always require more.
Security of the network
Security of the network is important for a crypto project to be trusted and ultimately widely used, but what exactly does security of the network mean? In a nutshell it means that the network is resistant from forms of malicious attacks which would change the valid and real ledger entries which record wallet balances, transactions, and unspent transactions. While there are many forms of attacks, the primary attack of focus is the infamous 51% attack (it’s been theoretically proven that realistically for most networks the actual percentage of control necessary is less than 40% but that’s beyond the scope of this article). Security of a network can be provided by either method, PoW or PoS, and that factor by itself doesn’t provide any tangible value to a projects token, only perceived value based on trust that the network is secure.
One of the biggest factors in preventing a hostile takeover of a PoS based network is naturally the price and volume of trading. A massive purchase would be easily detected and spike the price artificially, making it progressively more expensive to purchase a 51% controlling stake in the project/network. Naturally, there must also be supporting volume to do this, even if a slow-roll approach of small batch purchases over time was implemented. If there are not enough tokens in circulation overall, there just isn’t enough to acquire the amount needed.
One of the primary arguments for considering a PoS network is that the cost of making a 51% attack is increased exponentially under this system. However, if check-pointing is enabled that in and of itself is supposed to shield against attacks and not allow for a blockchain takeover. So, I would argue this point essentially cancels itself out. This would be true of most any project contemplating PoW or PoS.

Proof of Work based networks add a hardware factor into the equation, which subverts the price rising mechanic of simply buying on the exchange (we aren’t going to mix mining and buying for arguments sake, but a combination could naturally be used). There is a real cost to hardware however, and availability to everyone is tighter than what may be available to everyone on an exchange. There are also other factors that need to be considered. Operational expenses (opex) include not only the cost of electricity, but also the cost of facilities, mining technicians, bandwidth, and all the supporting peripherals that any mining farm must contend with. These costs are real to be sure, even if only some are reoccurring.
The point here is this type of argument is centered in the belief that the attackers’ motive is to destroy or capitalize on the value of the token. Whether it be to totally crush and kill the project or to cash out vast quantities. In truth this is highly unlikely to happen because of the very argument that it is expensive and with little to gain overall. The more appropriate argument to apply is the ability for a nation or state actor to gain substantial holdings and monitor information or subversively control the market (or attempt to). The most valuable information is that which is gathered through silently watching and observing without detection. In such a case, which is cheaper; investing enough capital to establish a strong base camp inside the network and watch quietly, or buy up a bunch of equipment, staff the facility to manage it, and pay enormous electric bills? I would opt for that PoS easy buy button myself.
Is there a “best” solution?
No system is fool proof, but the more roadblocks and gates you add the more difficult it becomes, in the end security is just that. The more gates I must go thru the less likely I will attempt to get through, until desperation or incentive becomes so great that the rewards outweigh the risks. There are also hybrid solutions such as DASH and their Chainlock solution which provide a high degree of certainty against reorganization, critical for accepting payments quickly; we will look at DASH specifically in a deep dive article in the future. Dash also happens to have a very high hashrate and price point secured by ASIC miners and Masternodes as well. In some cases just being large enough can be it’s own security measure (it’s getting there that can be tricky).
The sunken cost of hardware which can later be resold is an interesting argument, but unfortunately this only considers that a Mallory would buy hardware for a period and recoup all or most of its cost later. This only holds true for common hardware-based algorithms – those that center on CPU or GPU miners. ASIC based networks require single-use investments that cannot be resold for any other purpose.
For the most part the PoW vs PoS dilemma focuses eventually on the ASIC’s and their dominance, with centralized distribution channels. This makes it difficult for the smaller investors to gain real traction in any substantial way. In the case of Monero (XMR) which is soon to shift to the RandomX algorithm as a CPU centric algorithm, this may change that dynamic greatly. In an interesting twist of history, going back to a CPU focused algorithm allows once again common hardware to participate in mining. However, the sheer size and acceptance of Monero as the top privacy focused crypto currency means that there are already many miners ready to support the new algorithm. Those willing to commit massive resources to continue mining it. CPU hardware is readily available in data centers all over the world currently, and with a flip of a switch a docker image could be deployed to swarm hash rates on the network. This has occurred in the past with other algorithms and I suspect will occur again. It can also open opportunities for large investors and small investors alike to grab a part of the network hashrate, proportional to their means. There is not a severe bottleneck of specialized hardware made by only a few manufactures anymore. In the end the more distributed hash power there is, the more secure the network is.
Mining pools and their centralization of hashrate is a real problem however, so I haven’t forgot about that devil. It’s just outside the scope for this topic, I plan on addressing that separately in the future.
For the final part of the article, we will look at ASIC resistance, good or bad…
Author
Jim Andersen
Director, Mining Operations
LinkedIn
